Domino 10 beta & SSL Ciphers
For reasons unknown to me, this very old article is still getting a lot of attention. It is outdated. For handling SSL certificates with modern Domino versions, check out these articles:
Update: HCL assured me that in the Domino 10 Gold release below issue will be fixed. If there’s no SSLCipherSpec line in the notes.ini, Domino will automatically select the strong ciphers. Just as in the Domino 9.0.1 with the later fixpacks.
HCL is running a beta program for Domino V10. If you haven’t heard anything about Domino V10 yet and had any interest in Lotus/IBM Domino in the past, it might be about time to inform yourself as for the first time in 5 years, we actually get a new release of Domino and it will contain some features that are easy to get excited about. For more info on Domino V10, just Google though this blog article by Hogne Bo Petterson might be a good start. As I’m part of the Domino V10 beta program I’ll blog about it every now and then as I encounter things worth mentioning on the way.
Tonight I decided it was time to upgrade my Domino servers with Domino 10. Both were running on CentOS 7.5 already (which now is actually supported!), so that saved me from upgrading the OS (RedHat/CentOS 6 is no longer supported). The upgrade went smooth. Nothing worth mentioning there. After the upgrade I did see some alarming messages in the logs though:
04-09-2018 22:52:14.62 SSLDisableExportCiphers> Disabling weak cipher RSA_WITH_3DES_EDE_CBC_SHA. Set notes.ini "USE_WEAK_SSL_CIPHERS=1" to re-enable. 04-09-2018 22:52:14.62 SSLDisableExportCiphers> Disabling weak cipher RSA_WITH_RC4_128_SHA. Set notes.ini "USE_WEAK_SSL_CIPHERS=1" to re-enable. 04-09-2018 22:52:14.62 SSLDisableExportCiphers> Disabling weak cipher RSA_WITH_RC4_128_MD5. Set notes.ini "USE_WEAK_SSL_CIPHERS=1" to re-enable. 04-09-2018 22:52:14.62 SSLDisableExportCiphers> Disabling weak cipher RSA_WITH_DES_CBC_SHA. Set notes.ini "USE_WEAK_SSL_CIPHERS=1" to re-enable. 04-09-2018 22:52:14.62 SSLDisableExportCiphers> Server key (2048 bits) too strong for EXPORT1024 ciphers. Disabling cipher RSA_EXPORT1024_WITH_DES_CBC_SHA 04-09-2018 22:52:14.62 SSLDisableExportCiphers> Server key (2048 bits) too strong for EXPORT ciphers. Disabling cipher RSA_EXPORT_WITH_RC4_40_MD5
and
04-09-2018 22:36:36 TLS/SSL connection 192.168.7.150(51526) -> 192.168.7.100(443) failed with no supported ciphers 04-09-2018 22:44:48 TLS/SSL connection 192.168.7.100(20638) -> 192.168.7.100(465) failed with no supported ciphers 04-09-2018 22:52:14 TLS/SSL connection 192.168.7.173(42978) -> 192.168.7.100(636) failed with no supported ciphers
So why is Domino even starting about those weak ciphers which we haven’t used in ages and what’s happening with my web connections, LDAP connections and secure SMTP connections to my Domino server?!? A quick test showed that none of them were working anymore as they had no way of securely connecting to my Domino server. Time to start reading the documentation…
The documentation luckily did give me a hint what happened. Remember the line in your notes.ini SSLCipherSpec= with a bunch of ciphers? If you closely followed the latest fixpacks for Domino then you know that since Domino 9.0.1 FP4IF2 the advice was to remove that line from your notes.ini as Domino would then automatically use a secure list of ciphers. Apparently the developers didn’t actually expect you to follow the documentation of those fixpacks as they now wrote:
- Cipher configuration through the SSLCipherSpec server notes.ini setting that is
required for Domino 9.0.1 feature packs is no longer required as of Domino 10.
A value that you previously specified through the notes.ini setting is selected
automatically in the Server document of a Domino 10 server after upgrading
from Domino 9.0.1. After the upgrade, the notes.ini setting on the server is
ignored.- If you use Internet Site documents, the cipher selections in the previous site
documents are honored. This is a change in behavior from Domino 9.0.x when
cipher settings were controlled on a per-server basis through the SSLCipherSpec
notes.ini setting and cipher settings in Internet Site documents were ignored.
Since the Internet Site documents may have older cipher settings, evaluate them
after upgrading to Domino 10.
So yes, remember those really old ciphers in your internet site documents? Suddenly they’re used again, which is why I got the messages about those really old ciphers (and they weren’t used in the end as USE_WEAK_SSL_CIPHERS=1 wasn’t in my notes.ini). All the newer ciphers, which are the only ciphers which the connecting browsers, ldap clients etc use, are not selected by default.
So the solution, once you know what’s happening, is easy. Go through all your internet site documents and select the ciphers you want to allow.
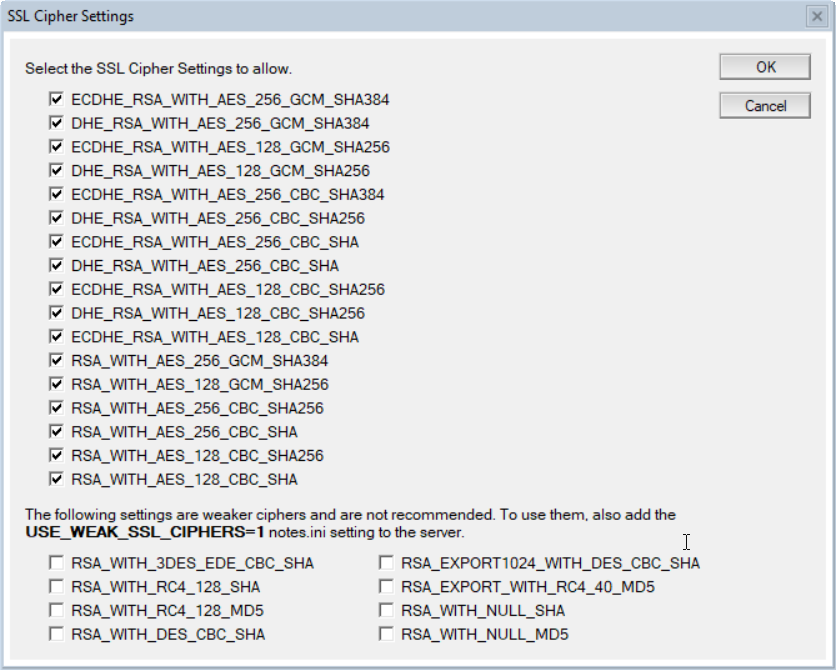
Of course *you* don’t need this info as you would do the upgrade the proper way: Update the design of your Domino directory on your administration server with the V10 Domino Directory design, read all the documentation, make the necessary changes to you server, configuration and internet site documents and only then upgrade your domino server. Just in case you slip somewhere in this procedure though, be warned about this one 😉


nice one. helps a lot!