Domino and Modern E-mail Server Operations
Last July, I presented a session for OpenNTF titled “How to use Domino as a Mail Server in a Modern World”. It was an in-depth session on the history of the SMTP protocol, new email security protocols and how to configure them to have the best chance that a mail from your domain will reach the intended recipient. Especially the first part was rather generic, so even if you’re the administrator of another mail server platform than HCL Domino, it might be of interest to you. You can find the presentation itself here, but there’s also a recording of the session:
What’s the deal with port 465
When I did my research for this session, I encountered something peculiar. There seems to be a lot of confusion on the internet around using port 465 for mail. I found multiple sites saying that this port was deprecated, but is that correct? I checked it out at the source, and the source for whether an internet protocol is deprecated or not are the RFCs from the IETF. I’ll give you the short version first, but you might want to read the longer version too, as it’s an interesting story. Short version: Port 465 is not deprecated for SMTP. It’s actually the preferred port for mail submission.
So, what’s the longer story? Before getting into that, it’s important to know that there’s a difference between mail relaying and mail submission or a Mail Transfer Agent (MTA) and a Mail Submission Agent (MSA).
Mail Transfer vs Mail Submission
Where the MTA is used for relaying mail between two mail servers, the Mail Submission Agent is used to submit a message to a mail server. Let’s put the differences in a table:
| Feature | MTA (Mail Transfer Agent) | MSA (Mail Submission Agent) |
|---|---|---|
| Purpose | Relays emails between servers (domains) | Submits email from client to server |
| Port | Primarily port 25 | Primarily port 587 or port 465 (for implicit TLS) |
| Authentication | Usually no client authentication (server-to-server) | Usually requires user authentication |
| Use Case | Server-to-server email transfer | User-to-server email submission |
| Security | STARTTLS is optional (for legacy connections) | STARTTLS or TLS encryption is mandatory |
| Example Software | Postfix, Sendmail, Exim, Domino | Postfix (configured for submission), Dovecot, Domino |
So where port 25 is the standard port between mail servers, port 587 and 465 are the default ports to submit mail to a mail server from a client (though port 25 is also in use for this function).
The thing with Domino is that it can perform both functions. It’s both a mail server that sends and receives mails to/from other domains, as a mail server that accepts mail submits from, usually, applications that need to send mail. Also, Domino itself can function as a mail client when it submits the mails to a relay host. A problem with Domino’s configuration is that you have to make a choice, as, in the ports section, it can’t distinguish between mail that’s submitted by a client and mail that’s coming from another server.
The history of port 465
But back to port 465. From the previous part, we learned that port 465 is meant for mail submission. Not mail transfer. So, where did the confusion whether it’s deprecated or not originate? Port 465 first popped up when the Internet Assigned Numbers Authority (IANA) assigned it for SMTPS (SMTP over SSL) in 1997. It was never properly documented in a formal RFC. Instead, it was listed briefly in the IANA registry. At the same time, IANA had assigned SSL ports for the IMAP and POP3 protocols and the feeling arose that there were a lot of ports assigned to mail protocols. Therefore, when RFC 2487 was published in 1998, which defined the STARTTLS extension for SMTP, allowing SMTP connections on port 587 to be upgraded to use TLS, IANA decided to unassign port 465. So starting in 1998, port 465 was deprecated for SMTP over SSL.
However, many mail systems included implicit TLS for mail protocols in their server configuration. For SMTP, there was no longer an official port for implicit TLS, but they had to provide a default. Despite being deprecated, they showed port 465 as the default, which kept it alive. This is, for example, the configuration form of Lotus Domino 5.0.3 which became available at the end of 2000. Lotus Domino was at the time the largest email-system in the world among the top 500 companies.
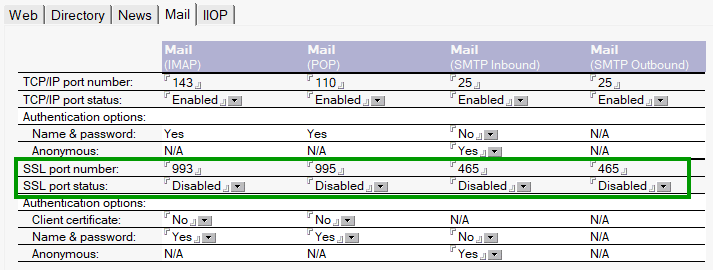
Compare it to the form that we find in the latest beta of Domino 14.5
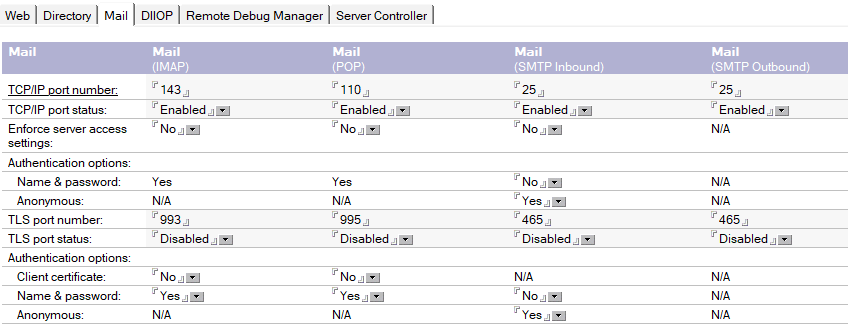
So while port 465 was deprecated, it kept on appearing in mail server configurations of many mail products, keeping it alive as the de facto standard for SMTP over implicit TLS.
So when RFC 8314 got published in 2018, which described Implicit TLS for SMTP Submission, they chose the obvious port for this service: Port 465. This RFC also states:
The STARTTLS mechanism on port 587 is relatively widely deployed due to the situation with port 465 (discussed in Section 7.3). This differs from IMAP and POP services where Implicit TLS is more widely deployed on servers than STARTTLS. It is desirable to migrate core protocols used by MUA software to Implicit TLS over time, for consistency as well as for the additional reasons discussed in Appendix A. However, to maximize the use of encryption for submission, it is desirable to support both mechanisms for Message Submission over TLS for a transition period of several years. As a result, clients and servers SHOULD implement both STARTTLS on port 587 and Implicit TLS on port 465 for this transition period.
So while port 587 with STARTTLS has to be supported for the time being by SMTP servers, implicit TLS over port 465 is the preferred protocol for mail submission.
DKIM implementation in HCL Domino
People who watched the presentation will have noticed that I wasn’t too complimentary on the implementation of DKIM in HCL Domino 12. The way it’s implemented is needlessly complex and, especially if you have multiple servers sending out SMTP mail that are not in a cluster, an administrator’s hell if ever you have to add or replace DKIM keys.
Daniel Nashed wrote a helper tool in Domino to make the administration effort a bit less, which he showed to me. The tool looks nice and definitely helps, but doesn’t solve the administration mess when multiple non-clustered servers need to send DKIM signed SMTP mails. I do hope that HCL will provide a proper solution for this in the next Domino version.
More SMTP security related protocols
I covered a lot in my session, but one and a half hour is simply not enough to cover all SMTP security related protocols. For example, I didn’t cover protocols like DANE, MTA-STS and TLS-RPT. I will cover those in a separate blog article where I’ll explain what they are, how to implement them and invite you to vote for an AHA idea to implement them in HCL Domino.


Thanks for the great explanation and OpenNTF video session! I totally agree on the implementation of DKIM and clusters, a nightmare.